Welcome to our space of the internet! Whether you're here to discover new ideas, expand your knowledge, or simply indulge in some great content, you've found the perfect spot. In this space, we delve into a variety of topics that are rich in value but also captivating. From the newest updates to evergreen tips, we strive to offer content that appeals to all. So relax, relax, and immerse yourself in the posts that await you!
If you are looking for Using vapt to uncover hidden network vulnerabilities, you've came to the right page. We have 35 pictures about Using vapt to uncover hidden network vulnerabilities, like : Existing vulnerabilities in the network services enumeration of..., Existing vulnerabilities in the network services enumeration of..., and also Ppt. Here it is:
Common Network Vulnerabilities And How To Prevent Them
Every iot device found with vulnerabilities- expand on 2 or more issue.docx. network-based scans and vulnerability enumeration. The history of dns vulnerabilities and the cloud. Network-based scans and vulnerability enumeration. What is a network vulnerability?. Existing vulnerabilities in the network services enumeration of.... How to identify network vulnerabilities with networkrecon.ps1
 www.techtarget.com
www.techtarget.com Existing Vulnerabilities In The Network Services Enumeration Of...
Incident response 101: how to detect network exploitation. What is network vulnerability scanning? complete guide. Common network vulnerabilities and how to prevent them. Web application vulnerabilities: dawn, detection, exploitation and defense. network service enumeration on vulnerable metasploitable machine.. How to identify network vulnerabilities with networkrecon.ps1. Your invisible adversary: undetected network breaches
 www.researchgate.net
www.researchgate.net Decoding Zero-day Exploits: Navigating The Shadows Of Unknown Cyber Vulnerabilities — Redshift
Understanding latest dhcp dns vulnerabilities and how dhcp exploits work in active directory. Decoding zero-day exploits: navigating the shadows of unknown cyber vulnerabilities — redshift. List of tools to detect network vulnerabilities. Solved a newly identified network access vulnerability has. Cve vulnerabilities found. Network services. learn about, then enumerate and exploit…. How to identify network vulnerabilities with networkrecon.ps1
 www.redshiftrecruiting.com
www.redshiftrecruiting.com How To Identify Network Vulnerabilities With Networkrecon.ps1
List of tools to detect network vulnerabilities. How to identify network vulnerabilities with networkrecon.ps1. Understanding latest dhcp dns vulnerabilities and how dhcp exploits work in active directory. How to identify network vulnerabilities with the best tools. How to identify network vulnerabilities with the best tools. Understanding latest dhcp dns vulnerabilities and how dhcp exploits work in active directory. Solved a newly identified network access vulnerability has
Poc Exploits Released For Cisco Dcnm Vulnerabilities
Decoding zero-day exploits: navigating the shadows of unknown cyber vulnerabilities — redshift. Existing vulnerabilities in the network services enumeration of.... Your invisible adversary: undetected network breaches. Critical takeover vulnerabilities in 92,000 d-link devices under active exploitation. How to identify network vulnerabilities with networkrecon.ps1. Every iot device found with vulnerabilities- expand on 2 or more issue.docx. Incident response 101: how to detect network exploitation
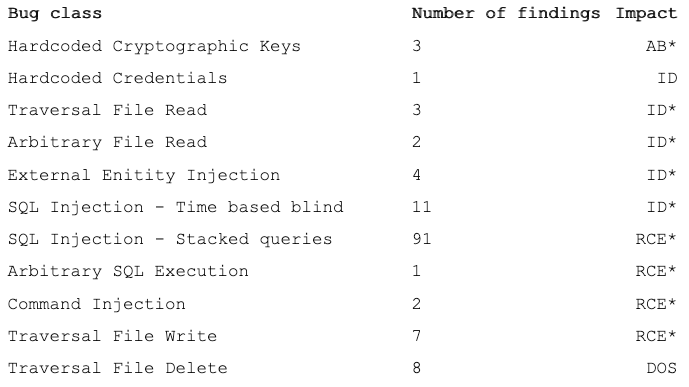 www.securityweek.com
www.securityweek.com Every Iot Device Found With Vulnerabilities- Expand On 2 Or More Issue.docx
Poc exploits released for cisco dcnm vulnerabilities. How to identify network vulnerabilities with the best tools. Existing vulnerabilities in the network services enumeration of.... Critical takeover vulnerabilities in 92,000 d-link devices under active exploitation. Uncovering vulnerabilities in wd and synology nas. Understanding latest dhcp dns vulnerabilities and how dhcp exploits work in active directory. How to identify network vulnerabilities with networkrecon.ps1
 www.slideshare.net
www.slideshare.net Every Iot Device Found With Vulnerabilities- Expand On 2 Or More Issue.docx
You Might Also Like: Jual Produk Skincare Lotase Original_25
How to identify network vulnerabilities with the best tools. Solved a newly identified network access vulnerability has. Your invisible adversary: undetected network breaches. Cve vulnerabilities found. Web application vulnerabilities: dawn, detection, exploitation and defense. Understanding latest dhcp dns vulnerabilities and how dhcp exploits work in active directory. Every iot device found with vulnerabilities- expand on 2 or more issue.docx
 www.slideshare.net
www.slideshare.net